PE Explorer gives you the power to look inside these PE binary files, perform static analysis, reveal a lot of information about the function of the executable, and collect as much information about the executable file as possible, without executing it. So why does this happen? The Malcode Analysis Pack, developed by David Zimmer, contains a series of utilities that were found to be necessary tools while doing rapid malcode analysis. By default, it will respond to DNS queries with the IP address of the host where the script is running, but this behavior can be modified using a command-line option. Did you like this? As a respected author and speaker, he has been advancing cybersecurity tradecraft and contributing to the community. 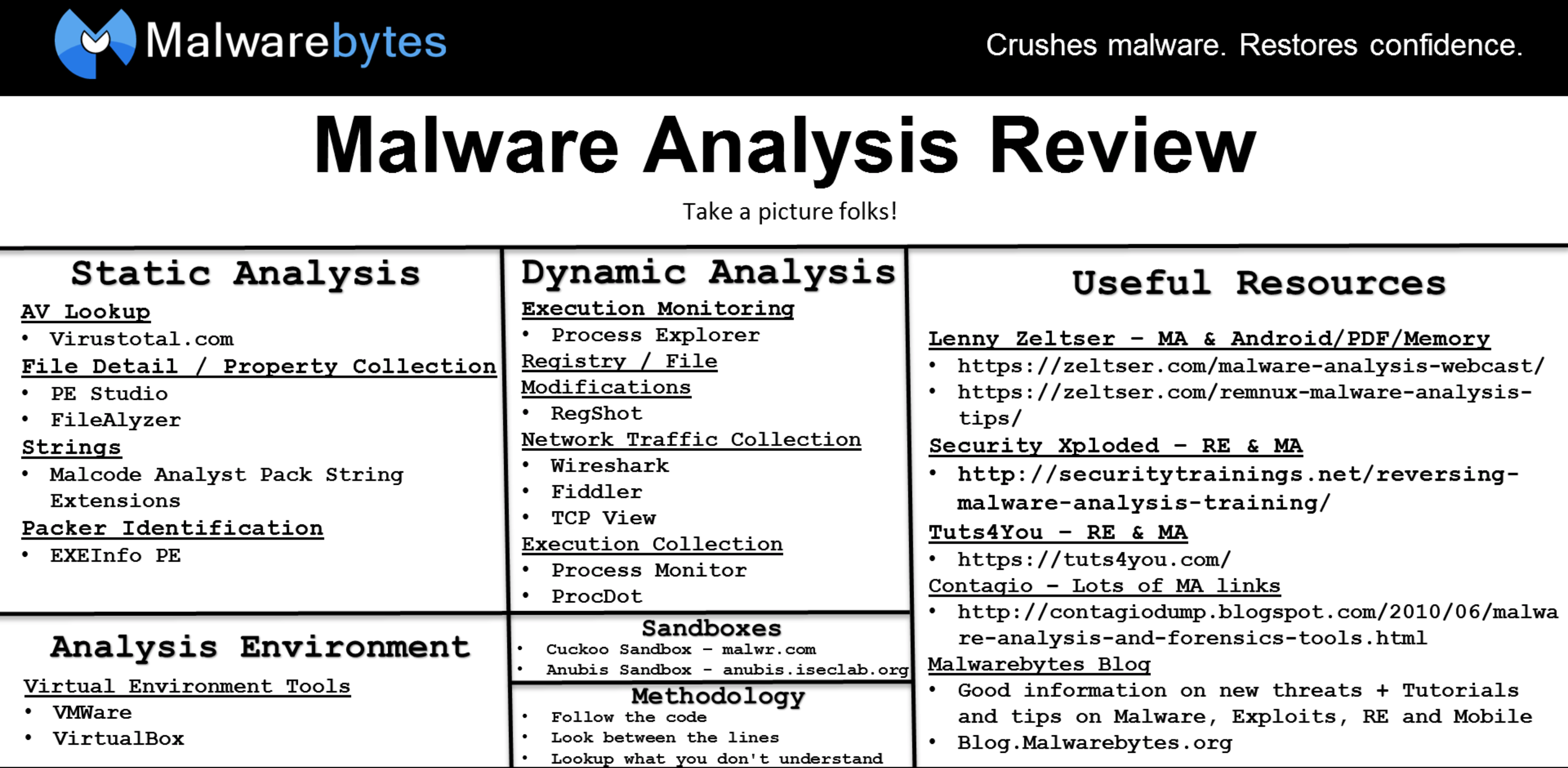
| Uploader: | Faezahn |
| Date Added: | 3 January 2007 |
| File Size: | 51.89 Mb |
| Operating Systems: | Windows NT/2000/XP/2003/2003/7/8/10 MacOS 10/X |
| Downloads: | 5863 |
| Price: | Free* [*Free Regsitration Required] |
From here, the tool allows you to explore the specific elements within an executable file.
The suite is available for x86 and x First PE editor with support for. Thank you BeesTeait is interesting link. Did you like this?

Since malicious software commonly uses hostnames when communicating with network resources, you can redirect such connections by defining the desired hostname to IP address mapping. Resource Editor Windows Vista icons supported capable of handling. Shellcode research and analysis application. ShellExt - This utility adds three shell extensions to the Windows Explorer right-click context menu: This is the same version that was used at the conference.
BeesTea Premium Member Jun SCLog - Shellcode research and testing application that loads and executes shellcode within the context of an API hooking framework.
iDEFENSE - Malcode Analysis Pack Software Release - Security | DSLReports Forums
More information and source code are available on the software releases page and the bundled installer. A version of this script is included in the REMnux Linux distribution. Not for use outside of lab VM environments. By default, it will respond to DNS queries with the IP address of the host where the script is running, but this behavior can be modified using a command-line option. LordPE is a tool e.
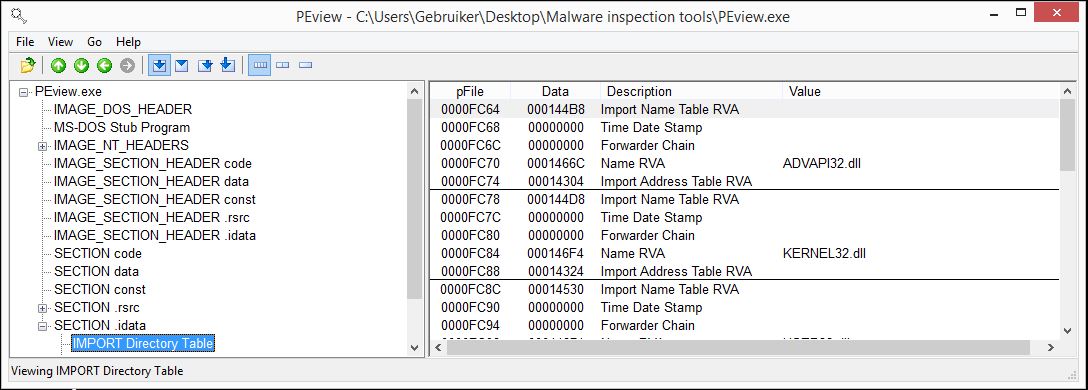
As a respected author and speaker, he has been advancing cybersecurity tradecraft and contributing to the community. PE Insider is a free Portable Executable viewer for the community. NET supportedutilities, rebuilder, hex editor, import adder, signature scanner, signature manager, extension support, scripting, disassembler, dependency walker etc.
The first official release will come soon.
[Resource] Malcode Analyst Tools Pack
The tool logs all DNS queries it processes. Fast, mlacode technique to get a readable disassembly for arbitrarily packed executables.
Over the past two decades, Lenny has been leading efforts to establish resilient security practices and solve hard security problems. Thanks for letting us know about them edit: Sign up for my newsletter if you'd like to receive a note from me whenever I publish an article or embark on a project.
Here are 3 free tools that can make aalysis easy to accomplish this. This feature displays the name, size and MD5 hash of all files in the specified folder in a popup form.
Malcode Analyst Pack
Follow me for more of the good stuff. It shares the same codebase for inspection as Cerbero Profiler and hence it supports the entire PE specification and is incredibly fast and stable. What's so great about Voip. Included in this package are: So why does this happen?
3 Free Tools to Fake DNS Responses for Malware Analysis
PE Explorer gives you the power to look inside these PE binary files, perform static analysis, reveal a lot of information about the function of the executable, and collect as much information about the executable file as possible, without executing it. Why is so difficult to fight ransomware??? Special fields description and modification.

No comments:
Post a Comment